PENTEST LAB – Drunk Admin Web Hacking Challenge 1
Description from Vulnhub
Configuration
The network is configured to obtain an IP address via DHCP by default. Although if you want to further configure the virtual machine you can login as user root and password toor. The apache web server is configured to run on port 8880.
Mission
The challenge includes an image hosting web service that has various design vulnerabilities. You must enumerate the various web service features and find an exploitable vulnerability in order to read system hidden files. The web application is 100% custom so do not try to search google for relative PoC exploit code.
FINAL GOAL: Reveal the hidden message for a date arrange that Bob sent to Alice.
Source: https://bechtsoudis.com/work-stuff/challenges/drunk-admin-web-hacking-challenge/
Solution
Run netdiscover -i eth0 -r 192.168.5.0/24
Run nmap -p 1-65535 -T4 -A -v 192.168.5.101 in zenmap
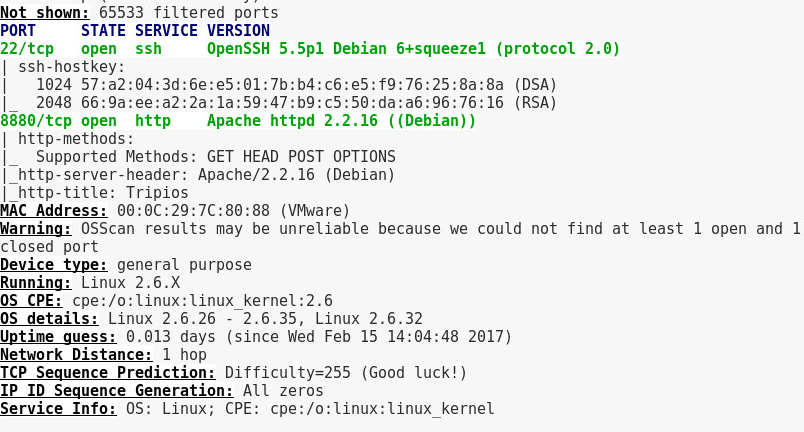
We found ssh port 22 aand 8880 apache running.
Here is what the site looks like:
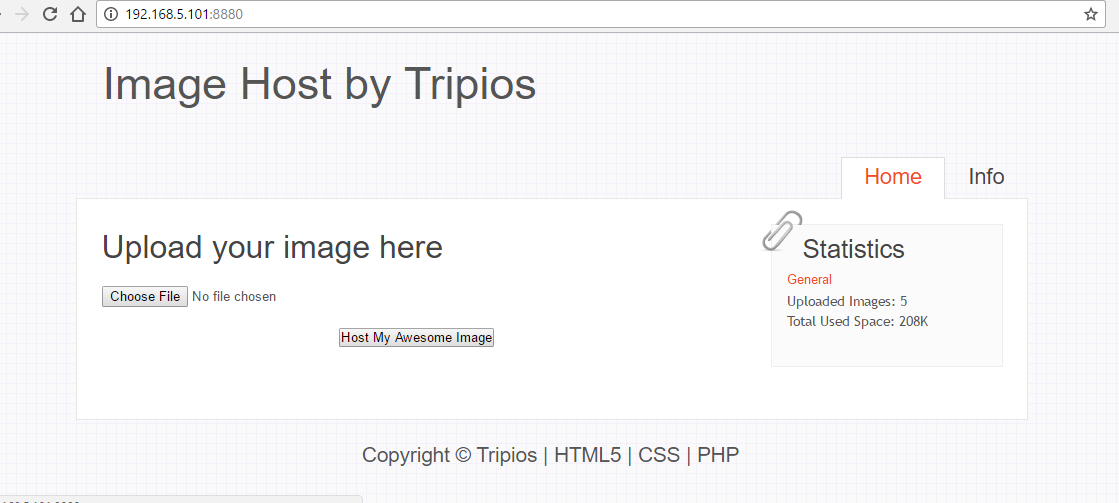
So, we upload a test image:
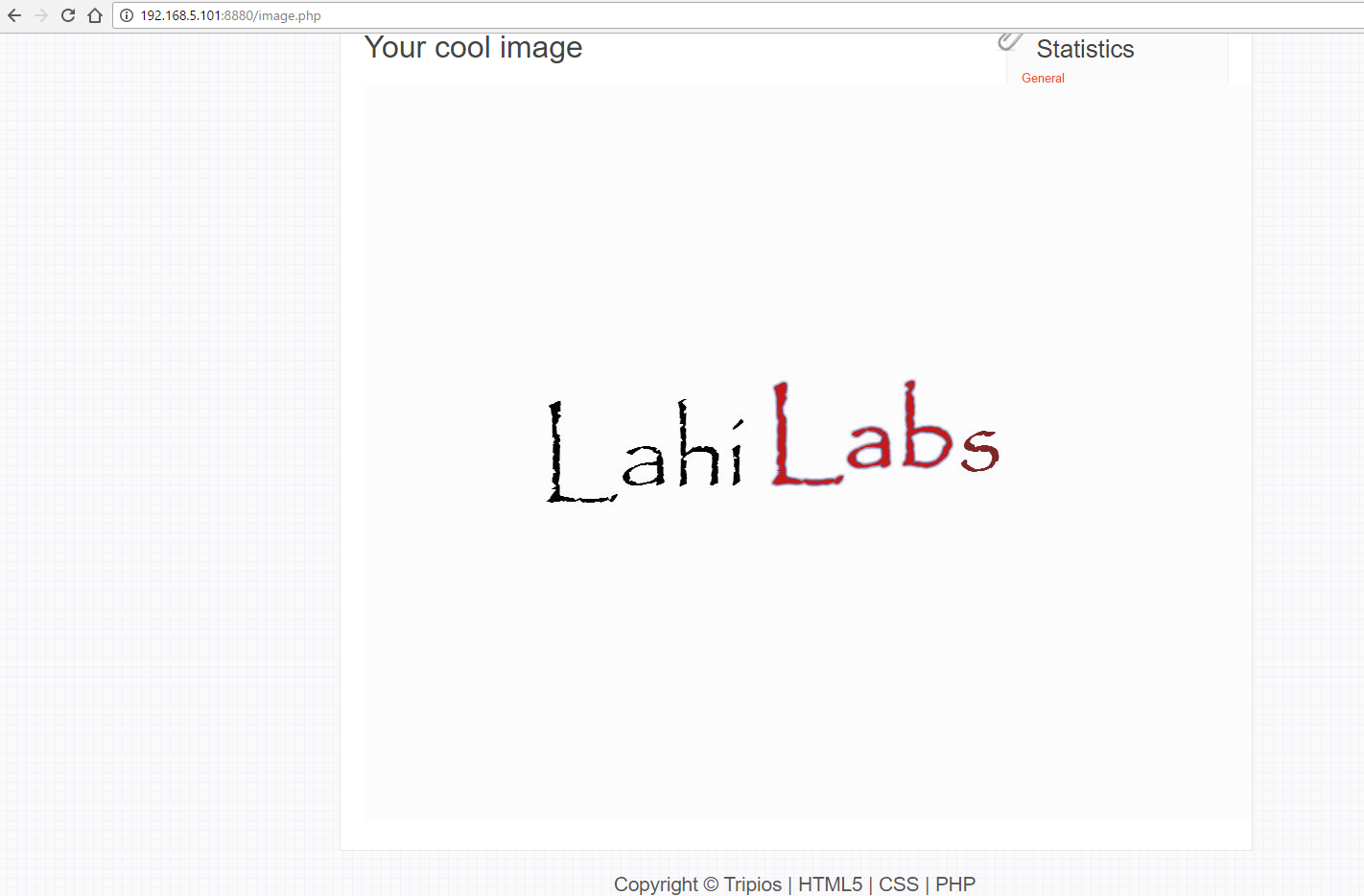
We check page source to see where this image is stored, and it looks like its stored in the “images/” folder and the original name” lahilab” is converted to a hash, 2e54303f51c2d22f5eab4855146c88d4
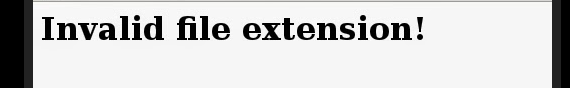
After a few test, we notice that we can only upload images in the format jpeg,gif and png. Anything else gives us the “Invalid extension “ error.
We need to upload a php script, but we still get this error.
After looking around, I realize we can change the name and use php.png and that worked.
This is all I needed and was able to write up. After uploading the php script, everything seemed to work. I didnt see the need to document everything after uploading the php script because there will be more similar CTFs that will show you how to use php scripts on vulnerable sites.
My takeaway: when straight php doesn’t work, try PHPABC.