How to Monitor SNMP devices with Telegraf and InfluxDB and Grafana | Meraki WAN Data
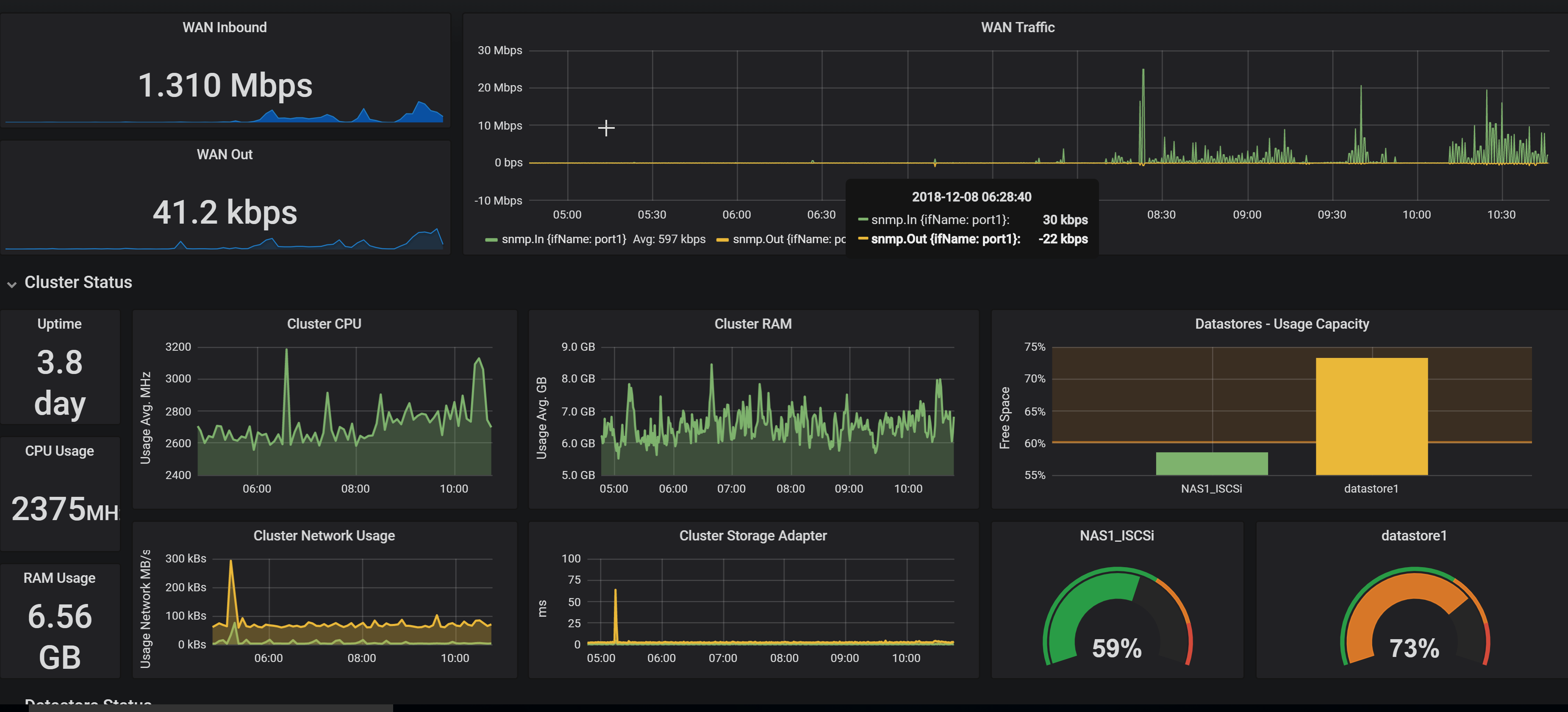
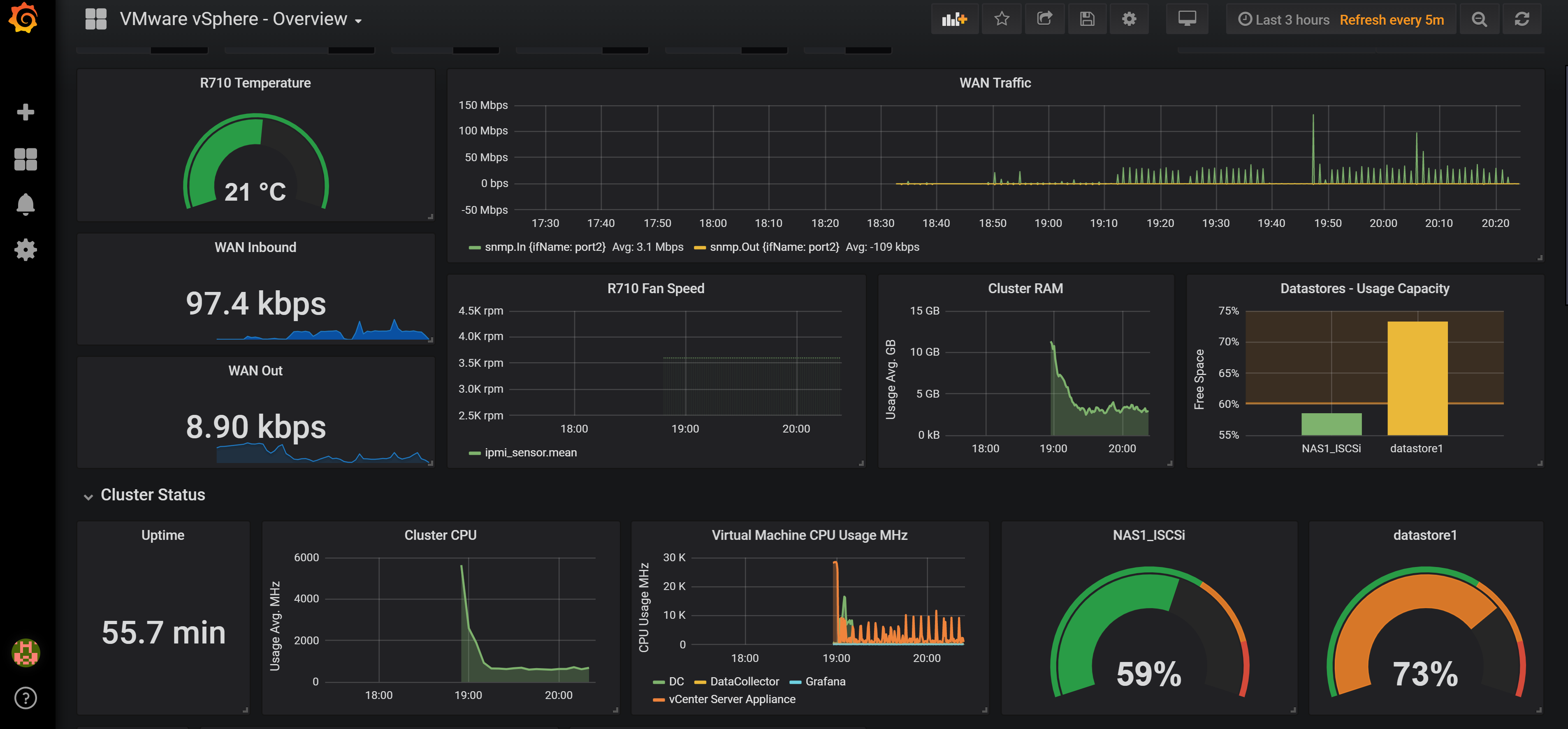
Why did i write this... Every IT admin needs to know what is going on in their environment at all times. Having a dashboard in your office on a TV and active alerts to your phone is critical in our careers. You ideally want to know about the problem before end users start calling. That’s why SNMP is very important and being able to use it to your advantage will make your life easier.